¶ Bucket management
Buckets are S3 folders for which various S3 properties can be configured.
Click on Buckets to get to the bucket management page.
¶ Bucket overview
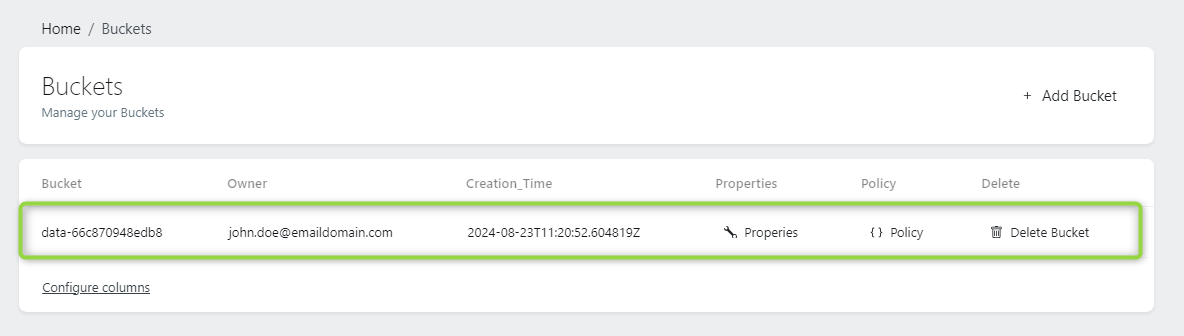
Here you can see your buckets, the name, owner, creation time. You can delete buckets, edit policies and properties here.
¶ Create bucket
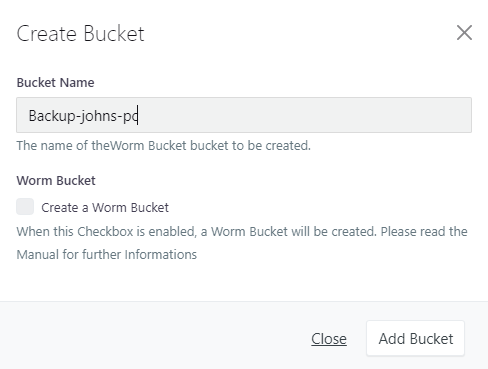
Click on “+ Add Bucket” to create a new bucket. Give the bucket a name and select whether the Worm Bucket property should be configured (detailed information “Worm Bucket / Object lock” can be found further down in the instructions. Then click on “Add Bucket”.
¶ Delete bucket

If you click on Delete Bucket, the bucket and the files in it will be permanently deleted.
¶ Properties
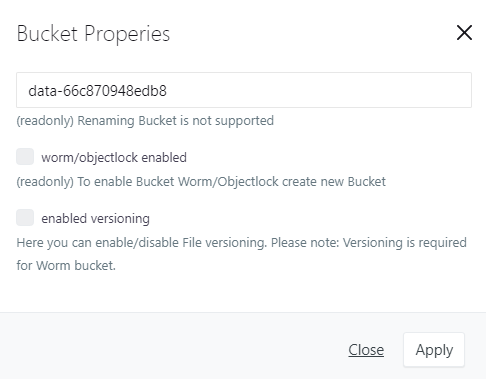
In the bucket properties you can see whether it is a worm bucket and whether versioning is configured. You can switch versioning on and off if it is not a worm bucket. If versioning is switched on, deleted, overwritten or modified files are retained. You can access older or deleted files when versioning is switched on.
¶ Bucket guidelines
You have the option of protecting your buckets with various guidelines and assigning guidelines.
To do this, click on Richline for the desired bucket.
A window opens with a blank page if no policy has been created yet.
The policy must be entered in a compatible format.
¶ Example
You want to grant a sub-user who has the authorization “none” read rights on a bucket “myPictures”.
{
"Version": "2012-10-17",
"Id": "uniqueID",
"Statement": [
{
"Sid": "BucketAllow",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam:::user/john.doe@emaildomain.com:subuser1"
]
},
"Action": [
"s3:ListBucket",
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::myPictures",
"arn:aws:s3:::myPictures/*"
]
}
]
}
A unique name or character string must be entered under “Id”: “uniqieID”, e.g. “allow-subuser1-read-mypictures”.
Under “arn:aws:iam:::user/...” the user who is to be granted rights must be entered, e.g. john.doe@emaildomain.com:subuser1.
Under “Resource”: the bucket or subfolder must be entered. e.g:
“arn:aws:s3:::myPictures” -> Rights for the bucket.
“arn:aws:s3:::myPictures"/* -> Rights for all subfolders.
For “Action”: “s3:ListBucket”, “s3:GetObject” -> Read rights.
For “Action”: “s3:ListBucket”, “s3:GetObject” -> Read rights.
¶ Example 2
You want to grant full access to a bucket “myPictures” to a sub-user who has the authorization “none”.
{
"Version": "2012-10-17",
"Id": "uniqueID",
"Statement": [
{
"Sid": "BucketAllow",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam:::user/john.doe@emaildomain.com:subuser1"
]
},
"Action": [
"s3:*"
],
"Resource": [
"arn:aws:s3:::myPictures",
"arn:aws:s3:::myPictures/*"
]
}
]
}
A unique name or character string must be entered under “Id”: “uniqieID”, e.g. “allow-subuser1-read-mypictures”.
Under “arn:aws:iam:::user/...” the user who is to be granted rights must be entered, e.g. john.doe@emaildomain.com:subuser1.
Under “Resource”: the bucket or subfolder must be entered. e.g:
“arn:aws:s3:::myPictures” -> Rights for the bucket.
“arn:aws:s3:::myPictures"/* -> Rights for all subfolders.
For “Action”: ["s3:*] -> All full access.
¶ Worm Bucket / Object lock
S3 Object Lock is a feature of Simple Storage Service (S3) that allows objects in an S3 bucket to be protected against accidental or malicious deletion or modification. This is often referred to as "Write Once, Read Many" (WORM). The S3 Object Lock feature ensures that data remains in an immutable state and cannot be changed or deleted for a specified period or indefinitely.
¶ How S3 Object Lock Works
S3 Object Lock offers two types of protection:
Governance Mode: In this mode, users with special permissions (e.g., administrators) can delete or modify objects before their retention period expires. Governance mode is ideal when organizations need an additional layer of protection but still want the flexibility to manage objects if needed.
Compliance Mode: This mode provides stricter protection. Once enabled, no user, not even an administrator, can delete or modify the object until the retention period expires. Compliance mode is ideal for scenarios where regulations require strict retention and protection of data.
In addition to the retention period, S3 Object Lock also offers the ability to set a Legal Hold on objects. This hold remains in place until it is explicitly removed, regardless of any set retention periods. This is useful when data needs to be preserved for legal proceedings.
¶ Benefits of S3 Object Lock
Data Integrity and Protection from Deletion: S3 Object Lock prevents data from being deleted or overwritten, which is particularly important to avoid accidental deletions or malicious activities.
Compliance with Legal Requirements: Many industries have strict retention requirements for data. With S3 Object Lock in Compliance mode, companies can ensure that their data remains unchanged for the legally required period.
Auditability: S3 Object Lock helps companies meet audit requirements by ensuring that data cannot be tampered with. This is especially important for companies that undergo regular audits or for whom data integrity is critical.
Flexibility: Governance mode offers flexibility in managing data, while Compliance mode allows for stricter controls. Companies can choose which mode is best suited to their specific needs.
Protection Against Ransomware: In times when ransomware attacks are increasing, S3 Object Lock provides additional protection, as attackers cannot delete or modify stored data even if they gain access to the system.
¶ Summary
S3 Object Lock is a valuable feature for organizations that need to ensure their data is secure, immutable, and protected for a specific period. Whether to protect against human error, comply with regulations, or safeguard against malicious attacks, S3 Object Lock provides a robust mechanism for data preservation and security.